Back to resources
Latest T-Mobile Attack Shows the Need for Zero Standing Privileges
September 2021 / 2 min. read /

Zero Standing Privileges
The T-Mobile hack that occurred last week underscored the need for organizations to enforce least privilege access to achieve zero standing privileges as soon as possible.
While many details of the hack remain unclear, the person identifying as the attacker claimed on Twitter that T-Mobile misconfigured a gateway GPRS support node that was used for testing. When the misconfiguration was posted online, the attacker gained access and eventually pivoted to T-Mobile’s LAN.
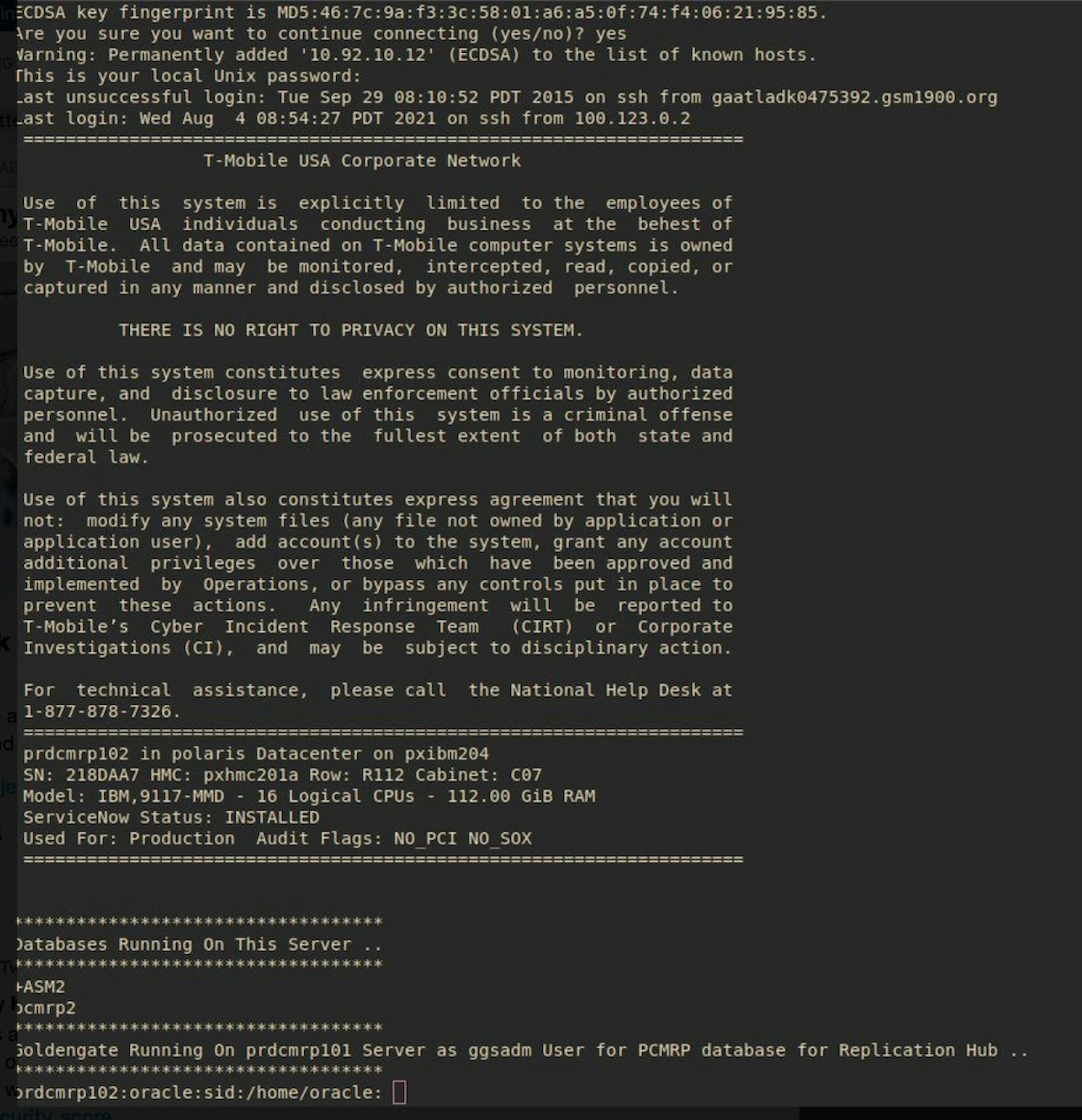
Eventually, the attacker said, they were able to “brute force/credential stuff SSH on more than 100+ servers, some Oracle.” Critically, the person also stated, “there was no rate limiting on those servers because they’re internal.”
Despite the fact the attack appears to be the result of lax on-prem security, it's important to remember that as organizations continue the great migration to multi-cloud environments, the steepest risk is the proliferation of identities and permissions cross-cloud that must be secured. In the case of the T-Mobile attack, if the hacker can be believed, the absence of rate-limiting allowed them to make thousands of requests, which led to the breach.
T-Mobile Hack
T-Mobile first confirmed data was stolen on Monday but the company didn’t share at that time what was stolen. The mobile carrier now says the compromised data of 48 million customers include first and last names, dates of birth, social security numbers, and driver’s license information. An additional 850,000 T-Mobile prepaid customer names, phone numbers, and account PINs were also compromised.
T-Mobile said they would issue free identity theft protection to their customers, but has not confirmed the nature of how the attack occurred. Consumer identity theft protection is a reasonable gesture, but given the repeated attacks targeting T-mobile, it seems there may be a deeper problem.
The clarion call here is that when zero standing privileges are not enforced properly, customer data, and the organization responsible for it, are both at extreme risk.
Here at Britive, we strongly urge companies working in multi-cloud environments to maintain zero standing privileges with self-service credential grants and auto expiration of privileges.

