Back to resources
What Organizations Need to Know about “Weakening Cloud Security”
September 2021 / 3 min. read /

Cloud Security
Unit 42 at Palo Alto Networks released an important report last week highlighting the increased risks organizations face due to deficient security surrounding Identity and Access Management (IAM) in cloud environments.
The report follows their 2020 Cloud Threat Report and found that “cloud environments are more susceptible to attacks today than in October 2020.” The report cites multi-factor authentication (MFA) misconfigurations and excessive permissions as two driving factors behind heightened risks to cloud security, particularly in AWS, Google Cloud, and Oracle Cloud.
The report notes:
Unit 42 researchers also found an increase in the number of organizations not rotating their IAM access keys and the number of organizations deploying overly privileged IAM accounts and roles. Similar to rotating user passwords, access keys must be rotated at least every 90 days to maintain minimal risk. Finally, the principle of least-privilege should be applied when creating and maintaining all IAM entities, be they users, roles or group privileges.
Here at Britive, we systematically stress the importance of visibility and detection across all cloud platforms. When an organization sees in real-time where misconfigurations are present and which users have excessive permissions, the task of effectively managing access becomes realistic.
We believe it is imperative to go beyond least privilege access (LPA).
Organizations should ensure all users accessing cloud environments – both human and machine IDs – have zero standing permissions (ZSP).
In the multi-cloud, ZSP is preferable to LPA because it minimizes risk and oversight responsibilities. Rather than granting access that may become excessive or unnecessary, organizations can instead eliminate standing privileges completely. Users that require access are issued just-in-time permissions (JIT), which are automatically revoked upon completing the task or when the allotted time expires.
Incorporating JIT access to resources as part of the CI/CD process can significantly bolster security cross-cloud without slowing down DevOps teams.
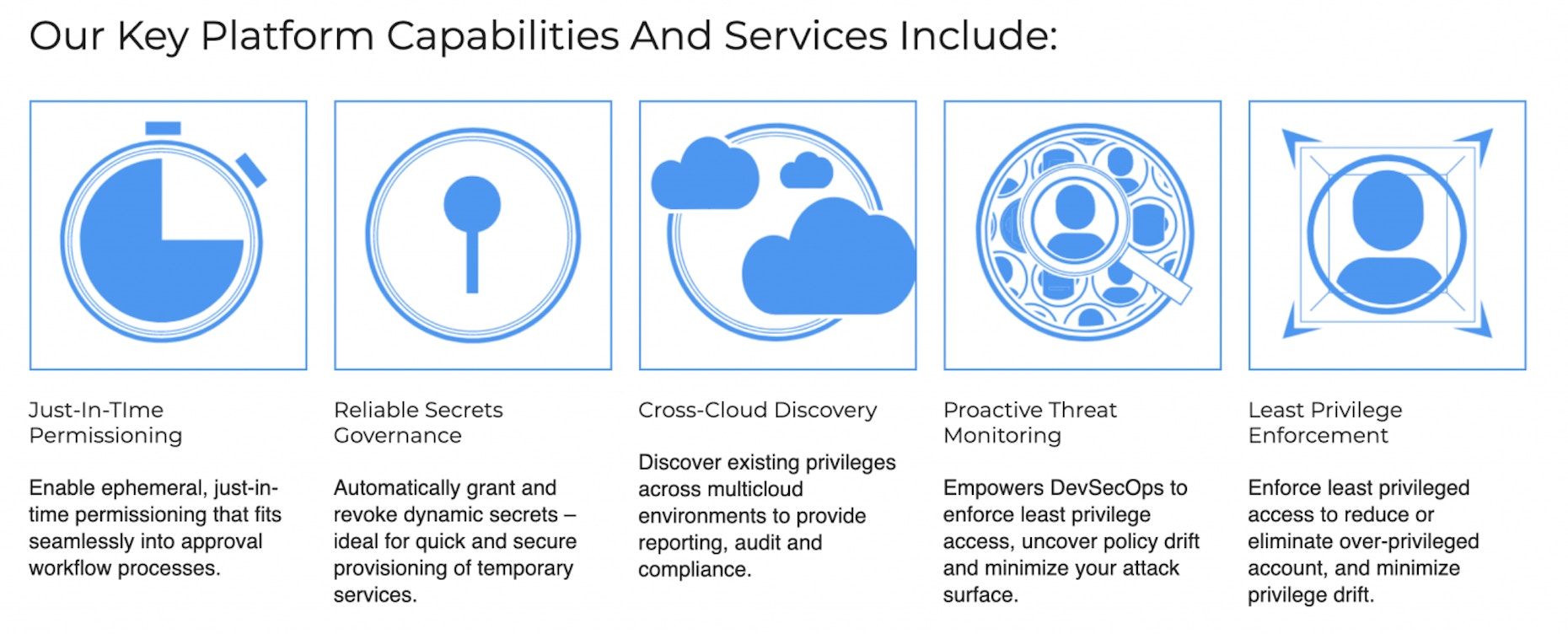
Traditional IAM, even when it is cross-cloud, is limited in its ability to manage privilege access. What’s more, monitoring the sheer number of users is a substantial challenge for organizations operating in multi-cloud environments. A cross-cloud privileged access management solution allows organizations to dramatically scale back the amount of time it takes to oversee access and simultaneously diminish the risk of human error. A true cloud-native PAM solution delivers complete visibility across CSPs, improves detection and monitoring, and provides analytics and reporting so teams can quickly evaluate who has access to which accounts.
To read more about managing and securing cloud privileges, download our free guide: “Six Best Practices for managing and Securing Cloud Privileges.”
You can get up and running on Britive in minutes, with minimal privileges required, and steer your organization away from the instances of weakened cloud security Unit 42 covered in its report.

